Every time we go online, we are exposed to all types of threats that are looking for the smallest weakness in our connection to try and take as much sensitive information as possible. One of those threats is called Man in The Middle. Never heard of it? With so many threats out there, it’s very hard to keep track of all of them, but it’s one you need to protect yourself from.
Is Your Browser Safe?
Man in the Middle Attacks is when someone intercepts a communication between two people and their systems and eavesdrops in their conversation. This person will relay messages between these two people and can capture and change relevant information in real-time. So, you won’t actually be getting what the other person is really saying and can easily be tricked into giving sensitive information when the other person never asked you for it.
How can this person gain access? A common way is using a malignant router on one either side of the two systems or Malware, Phishing, DNS Spoofing and that is why one should always have a good antivirus software. This will give the hacker access to the user’s web browser and information during the conversation.

Let’s say you want to check your Email, and you decide to use the public WiFi signal that is exactly what the hacker wants you to do to gain access to your account and your sensitive information.
This hacker can intercept your connection between you and the signal. The hacker will now have access to everything you are doing on your device. If you send and Email to a friend on this public WiFi signal, what the hacker does is that he/she can divert that Email to read it and change anything on it before sending to whomever you were going to send it to. Scary, right? Gives me the willies. That is the main reason why I never use public WiFi, Better safe than sorry.
The attack can only succeed if the hacker can impersonate each victim without the other one noticing anything unusual and most of the time the two victims don’t see anything until it’s too late. The bad news is that in HTTP it is tough to perceive Man in The Middle Attacks, but if you are using https, you should get a warning from your browser. That way you know you are at risk, but you may get such a warning if the hacker has already gotten into your system or the system at the other end.
How to Detect Man in The Middle Attacks
A way you can spot a man in the middle attack is y paying attention to a certificate error you might get if you were trying to log on to do online banking. The error message would say that your bank’s websites lack the valid encryption certificate. Please don’t click on this error message and ignore it, you got it for a reason.
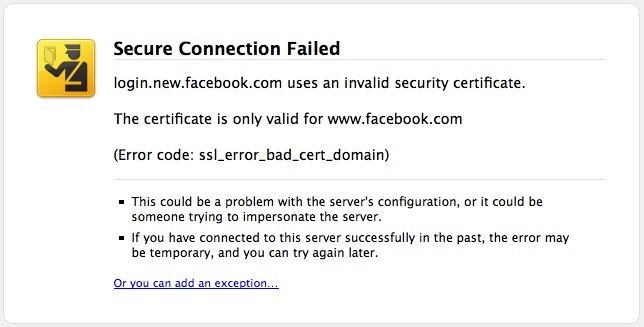
Another way you can become a victim of a Man in The Middle attack is when you do sensitive online stuff such as login to your bank account. If you see that your bank’s page is on HTTP, then I wouldn’t log in. Banks usually have HTTPS, so every time you do want to do any transactions that involve sensitive information, look for the S.
How to Protect Yourself Against Man in The Middle Attacks
Remember, if you want to stay safe against Man in the Middle attacks, there are some things you keep in mind. Don’t dismiss certificate warning since they show up because something is just not right. The reason why many choose to ignore is that they think that it is because of a misconfigured server. It’s better to figure out if that is the case than click through and suffer the consequences.

Always have a good antivirus on your computer such as Eset (which is what I use on one of my computer’s and have been using it for years. Excellent software and keeps me safe. Ah, one more thing, please try not to login into your sensitive accounts on public WiFi, it’s just not a good idea.
Read also: Shopping Tips to Keep You Safe Online
Conclusion
Man in the Middle Attacks are usually not within our control, but like you just read, there are things you can do to keep your info safe. How do you practice online safety? Let me know in the comments and don’t forget to give the post a share.